A digital
code that can be attached to an electronically transmitted message that
uniquely identifies the sender. Like a written signature, the purpose of
a digital signature is to guarantee that the individual sending the
message really is who he or she claims to be. Digital signatures are
especially important for electronic commerce and are a key component of most authentication schemes. To be effective, digital signatures must be unforgeable. There are a number of different encryption techniques to guarantee this level of security.
A diagram showing how a digital signature is applied and then verified below.
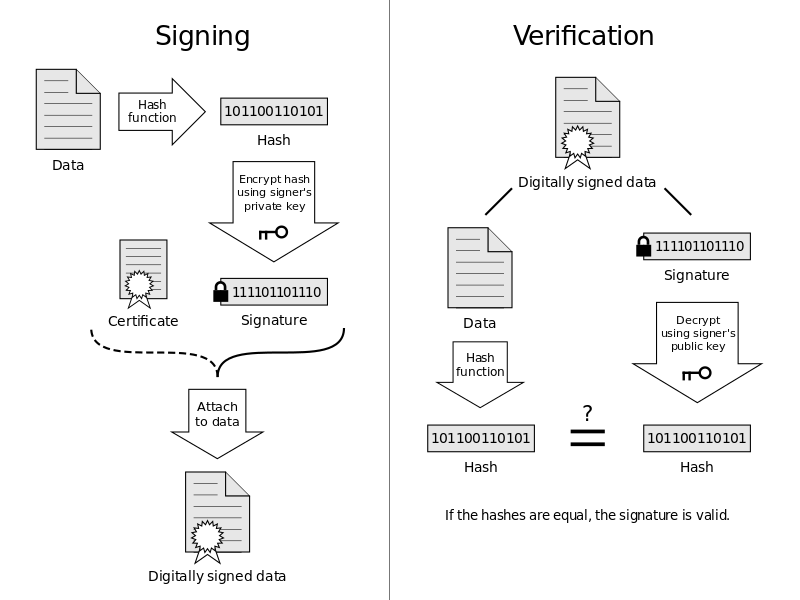
Digital signatures are often used to implement electronic signatures, a broader term that refers to any electronic data that carries the intent of a signature, but not all electronic signatures use digital signatures.[In some countries, including the United States, India, Brazil]and members of the European Union, electronic signatures have legal significance.
Digital signatures employ a type of asymmetric cryptography. For messages sent through a nonsecure channel, a properly implemented digital signature gives the receiver reason to believe the message was sent by the claimed sender. Digital signatures are equivalent to traditional handwritten signatures in many respects, but properly implemented digital signatures are more difficult to forge than the handwritten type. Digital signature schemes, in the sense used here, are cryptographically based, and must be implemented properly to be effective. Digital signatures can also provide non-repudiation, meaning that the signer cannot successfully claim they did not sign a message, while also claiming their private key remains secret; further, some non-repudiation schemes offer a time stamp for the digital signature, so that even if the private key is exposed, the signature is valid. Digitally signed messages may be anything representable as a bitstring: examples include electronic mail, contracts, or a message sent via some other cryptographic protocol.
Below are some common reasons for applying a digital signature to communications:
A diagram showing how a digital signature is applied and then verified below.

Digital signatures are often used to implement electronic signatures, a broader term that refers to any electronic data that carries the intent of a signature, but not all electronic signatures use digital signatures.[In some countries, including the United States, India, Brazil]and members of the European Union, electronic signatures have legal significance.
Digital signatures employ a type of asymmetric cryptography. For messages sent through a nonsecure channel, a properly implemented digital signature gives the receiver reason to believe the message was sent by the claimed sender. Digital signatures are equivalent to traditional handwritten signatures in many respects, but properly implemented digital signatures are more difficult to forge than the handwritten type. Digital signature schemes, in the sense used here, are cryptographically based, and must be implemented properly to be effective. Digital signatures can also provide non-repudiation, meaning that the signer cannot successfully claim they did not sign a message, while also claiming their private key remains secret; further, some non-repudiation schemes offer a time stamp for the digital signature, so that even if the private key is exposed, the signature is valid. Digitally signed messages may be anything representable as a bitstring: examples include electronic mail, contracts, or a message sent via some other cryptographic protocol.
How It Works
Assume you were going to send the draft of a contract to your lawyer in another town. You want to give your lawyer the assurance that it was unchanged from what you sent and that it is really from you.- You copy-and-paste the contract (it's a short one!) into an e-mail note.
- Using special software, you obtain a message hash (mathematical summary) of the contract.
- You then use a private key that you have previously obtained from a public-private key authority to encrypt the hash.
- The encrypted hash becomes your digital signature of the message. (Note that it will be different each time you send a message.)
- To make sure it's intact and from you, your lawyer makes a hash of the received message.
- Your lawyer then uses your public key to decrypt the message hash or summary.
- If the hashes match, the received message is valid.
Applications of digital signatures
As organizations move away from paper documents with ink signatures or authenticity stamps, digital signatures can provide added assurances of the evidence to provenance, identity, and status of an electronic document as well as acknowledging informed consent and approval by a signatory. The United States Government Printing Office (GPO) publishes electronic versions of the budget, public and private laws, and congressional bills with digital signatures. Universities including Penn State, University of Chicago, and Stanford are publishing electronic student transcripts with digital signatures.Below are some common reasons for applying a digital signature to communications:
No comments:
Post a Comment
its cool