click here complete Lecture Notes: Computer Networks
ISO-OSI 7-Layer Network Architecture
This lecture introduces the ISO-OSI layered architecture of Networks. According to the ISO standards, networks have been divided into 7 layers depending on the complexity of the fucntionality each of these layers provide. The detailed description of each of these layers is given in the notes below. We will first list the layers as defined by the standard in the increasing order of function complexity:
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
Physical Layer
This layer is the lowest layer in the OSI model. It helps in the transmission of data between two machines that are communicating through a physical medium, which can be optical fibres,copper wire or wireless etc. The following are the main functions of the physical layer:- Hardware Specification: The details of the physical cables, network interface cards, wireless radios, etc are
a part of this layer.
Coaxial Cable Hybrid Cable Wireless Card Network Card 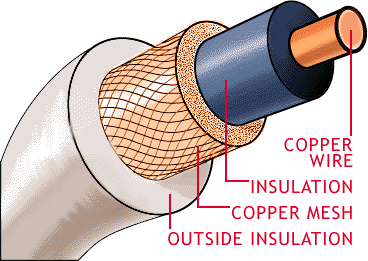



- Encoding and Signalling: How are the bits encoded in the medium is also decided by this layer. For example,
on the coppar wire medium, we can use differnet voltage levels for a certain time interval to represent '0' and '1'.
We may use +5mV for 1nsec to represent '1' and -5mV for 1nsec to represent '0'. All the issues of modulation is dealt
with in this layer. eg, we may use Binary phase shift keying for the representation of '1' and '0' rather than using
different volatage levels if we have to transfer in RF waves.
Binary Phase Shift Keyingclick here complete Lecture Notes: Computer Networks
- Data Transmission and Reception: The transfer of each bit of data is the responsibility of this layer. This layer assures the transmissoin of each bit with a high probability. The transmission of the bits is not completely reliable as their is no error correction in this layer.
- Topology and Network Design: The network design is the integral part of the physical layer. Which part of the
network is the router going to be placed, where the switches will be used, where we will put the hubs, how many machines
is each switch going to handle, what server is going to be placed where, and many such concerns are to be taken care
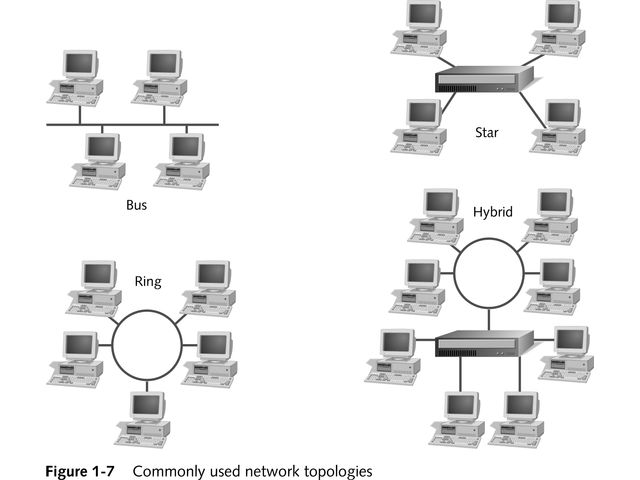
of by the physical layer. The variosu kinds of netopologies that we decide to use may be ring, bus, star or a hybrid of
these topologies depending on our requirements.
Data Link Layer
This layer provides reliable transmission of a packet by using the services of the physical layer which transmits bits over the medium in an unreliable fashion. This layer is concerned with :- Framing : Breaking input data into frames (typically a few hundred bytes) and caring about the frame boundaries and the size of each frame.
- Acknowledgment : Sent by the receiving end to inform the source that the frame was received without any error.
- Sequence Numbering : To acknowledge which frame was received.
- Error Detection : The frames may be damaged, lost or duplicated leading to errors.The error control is on link to link basis.
- Retransmission : The packet is retransmitted if the source fails to receive acknowledgment.
- Flow Control : Necessary for a fast transmitter to keep pace with a slow receiver.
Data Link Layer
Network Layer
Its basic functions are routing and congestion control.Routing: This deals with determining how packets will be routed (transferred) from source to destination. It can be of three types :
- Static : Routes are based on static tables that are "wired into" the network and are rarely changed.
- Dynamic : All packets of one application can follow different routes depending upon the topology of the network, the shortest path and the current network load.
- Semi-Dynamic : A route is chosen at the start of each conversation and then all the packets of the application follow the same route.
Routing
The services provided by the network can be of two types :
- Connection less service: Each packet of an application is treated as an independent entity. On each packet of the application the destination address is provided and the packet is routed.
- Connection oriented service: Here, first a connection is established and then all packets of the application follow the same route. To understand the above concept, we can also draw an analogy from the real life. Connection oriented service is modeled after the telephone system. All voice packets go on the same path after the connection is established till the connection is hung up. It acts like a tube ; the sender pushes the objects in at one end and the receiver takes them out in the same order at the other end. Connection less service is modeled after the postal system. Each letter carries the destination address and is routed independent of all the others. Here, it is possible that the letter sent first is delayed so that the second letter reaches the destination before the first letter.
Internetworking: Internetworks are multiple networks that are connected in such a way that they act as one large network, connecting multiple office or department networks. Internetworks are connected by networking hardware such as routers, switches, and bridges.Internetworking is a solution born of three networking problems: isolated LANs, duplication of resources, and the lack of a centralized network management system. With connected LANs, companies no longer have to duplicate programs or resources on each network. This in turn gives way to managing the network from one central location instead of trying to manage each separate LAN. We should be able to transmit any packet from one network to any other network even if they follow different protocols or use different addressing modes.
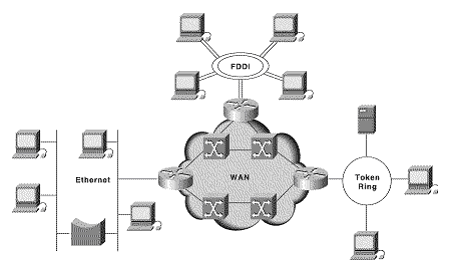
Inter-Networking
Network Layer does not guarantee that the packet will reach its intended destination. There are no reliability guarantees.
Transport Layer
Its functions are :- Multiplexing / Demultiplexing : Normally the transport layer will create distinct network connection for each transport connection required by the session layer. The transport layer may either create multiple network connections (to improve throughput) or it may multiplex several transport connections onto the same network connection (because creating and maintaining networks may be expensive). In the latter case, demultiplexing will be required at the receiving end. A point to note here is that communication is always carried out between two processes and not between two machines. This is also known as process-to-process communication.
- Fragmentation and Re-assembly : The data accepted by the
transport layer from the session layer is split up into smaller units
(fragmentation) if needed and then passed to the network layer.
Correspondingly, the data provided by the network layer to the transport
layer on the receiving side is re-assembled.
Fragmentation Reassembly 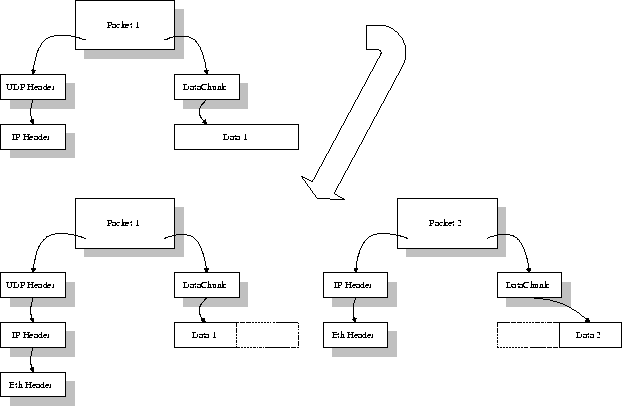
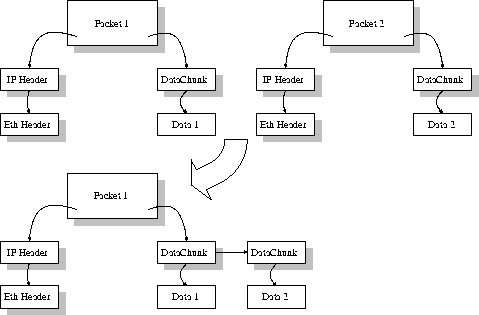
- Types of service : The transport layer also decides the type of service that should be provided to the session layer. The service may be perfectly reliable, or may be reliable within certain tolerances or may not be reliable at all. The message may or may not be received in the order in which it was sent. The decision regarding the type of service to be provided is taken at the time when the connection is established.
- Error Control : If reliable service is provided then error detection and error recovery operations are also performed. It provides error control mechanism on end to end basis.
- Flow Control : A fast host cannot keep pace with a slow one. Hence, this is a mechanism to regulate the flow of information.
- Connection Establishment / Release : The transport layer
also establishes and releases the connection across the network. This
requires some sort of naming mechanism so that a process on one machine
can indicate with whom it wants to communicate.
Session Layer
It deals with the concept of Sessions i.e. when a user logins to a remote server he should be authenticated before getting access to the files and application programs. Another job of session layer is to establish and maintain sessions. If during the transfer of data between two machines the session breaks down, it is the session layer which re-establishes the connection. It also ensures that the data transfer starts from where it breaks keeping it transparent to the end user. e.g. In case of a session with a database server, this layer introduces check points at various places so that in case the connectoin is broken and reestablished, the transition running on the database is not lost even if the user has not committed. This activity is called Synchronization. Another function of this layer is Dialogue Control which determines whose turn is it to speak in a session. It is useful in video conferencing.Presentation Layer
This layer is concerned with the syntax and semantics of the information transmitted. In order to make it possible for computers with different data representations to communicate data structures to be exchanged can be defined in abstract way alongwith standard encoding. It also manages these abstract data structres and allows higher level of data structres to be defined an exchange. It encodes the data in standard agreed way(network format). Suppose there are two machines A and B one follows 'Big Endian' and other 'Little Endian' for data representation. This layer ensures that the data transmitted by one gets converted in the form compatibale to othe machine. This layer is concerned with the syntax and semantics of the information transmitted.In order to make it possible for computers with different data representations to communicate data structures to be exchanged canbe defined in abstract way alongwith standard encoding. It also manages these abstract data structres and allows higher level of data structres to be defined an exchange. Other functions include compression, encryption etc.Application Layer
The seventh layer contains the application protocols with which the user gains access to the network. The choice of which specific protocols and their associated functions are to be used at the application level is up to the individual user. Thus the boundary between the presentation layer and the application layer represents a separation of the protocols imposed by the network designers from those being selected and implemented by the network users.For example commonly used protocols are HTTP(for web browsing), FTP(for file transfer) etc.Network Layers as in Practice
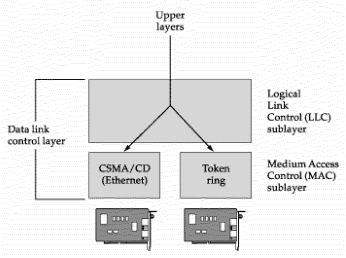
In most of the networks today, we do not follow the OSI model of seven layers. What is actually implemented is as follows. The functionality of Application layer and Presentation layer is merged into one and is called as the Application Layer. Functionalities of Session Layer is not implemented in most networks today. Also, the Data Link layer is split theoretically into MAC (Medium Access Control) Layer and LLC (Link Layer Control). But again in practice, the LLC layer is not implemented by most networks. So as of today, the network architecture is of 5 layers only.
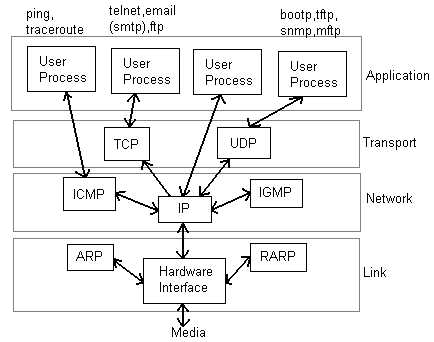
Network Layers in Internet Today
Some Related Links on OSI Model and TCP Model
Physical Layer
Types of Medium
Medium can be classified into 2 categories.- Guided Media : Guided media means that signals is guided by the prescence of physical media i.e. signals are under control and remains in the physical wire. For eg. copper wire.
- Unguided Media : Unguided Media means that there is no physical path for the signal to propogate. Unguided media are essentially electro-magnetic waves. There is no control on flow of signal. For eg. radio waves.
Communication Links
In a nework nodes are connected through links. The communication through links can be classified as- Simplex : Communication can take place only in one direction. eg. T.V broadcasting.
- Half-duplex : Communication can take place in one direction at a time. Suppose node A and B are connected then half-duplex communication means that at a time data can flow from A to B or from B to A but not simultaneously. eg. two persons talking to each other such that when speaks the other listens and vice versa.
- Full-duplex : Communication can take place simultaneously in both directions. eg. A discussion in a group without discipline.
- Point to Point : In this communication only two nodes are connected to each other. When a node sends a packet then it can be recieved only by the node on the other side and none else.
- Multipoint : It is a kind of sharing communication, in which signal can be recieved by all nodes. This is also called broadcast.
- Attenuation : When a signal transmitts in a network then the quality of signal degrades as the signal travels longer distances in the wire. This is called attenuation. To improve quality of signal amplifiers are used at regular distances.
- Noise : In a communication channel many signals transmits simultaneously, certain random signals are also present in the medium. Due to interference of these signals our signal gets disrupted a bit.
Bandwidth
Bandwidth simply means how many bits can be transmitted per second in the communication channel. In technical terms it indicates the width of frequency spectrum.Transmission Media
Guided Transmission MediaIn Guided transmission media generally two kind of materials are used.
- Copper
- Coaxial Cable
- Twisted Pair
- Optical Fiber
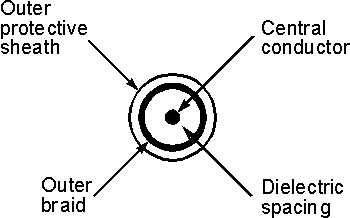
- Coaxial Cable:
Coaxial cable consists of an inner conductor and an outer conductor
which are seperated by an insulator. The inner conductor is usually
copper. The outer conductor is covered by a plastic jacket. It is named
coaxial because the two conductors are coaxial. Typical diameter of
coaxial cable lies between 0.4 inch to 1 inch. The most application of
coaxial cable is cable T.V. The coaxial cable has high bandwidth,
attenuation is less.
- Twisted Pair:
A Twisted pair consists of two insulated copper wires, typically 1mm
thick. The wires are twisted togather in a helical form the purpose of
twisting is to reduce cross talk interference between several pairs.
Twisted Pair is much cheaper then coaxial cable but it is susceptible to
noise and electromagnetic interference and attenuation is large.

Twisted Pair can be further classified in two categories:
Unshielded twisted pair: In this no insulation is provided, hence they are susceptible to interference.
Shielded twisted pair: In this a protective thick insulation is provided but shielded twisted pair is expensive and not commonly used. The most common application of twisted pair is the telephone system. Nearly all telephones are connected to the telephone company office by a twisted pair. Twisted pair can run several kilometers without amplification, but for longer distances repeaters are needed. Twisted pairs can be used for both analog and digital transmission. The bandwidth depends on the thickness of wire and the distance travelled. Twisted pairs are generally limited in distance, bandwidth and data rate. - Optical Fiber:
In optical fiber light is used to send data. In general terms prescence
of light is taken as bit 1 and its absence as bit 0. Optical fiber
consists of inner core of either glass or plastic. Core is surrounded by
cladding of the same material but of different refrective index. This
cladding is surrounded by a plastic jacket which prevents optical fiber
from electromagnetic interferrence and harshy environments. It uses the
principle of total internal reflection to transfer data over optical
fibers. Optical fiber is much better in bandwidth as compared to copper
wire, since there is hardly any attenuation or electromagnetic
interference in optical wires. Hence there is less requirement to
improve quality of signal, in long distance transmission. Disadvantage
of optical fiber is that end points are fairly expensive. (eg. switches)
Differences between different kinds of optical fibers:
- Depending on material
- Made of glass
- Made of plastic.
- Depending on radius
- Thin optical fiber
- Thick optical fiber
- Depending on light source
- LED (for low bandwidth)
- Injection lased diode (for high bandwidth)
- Depending on material
Wireless Transmission
- Radio: Radio is a general term that is used for any kind of frequency. But higher frequencies are usually termed as microwave and the lower frequency band comes under radio frequency. There are many application of radio. For eg. cordless keyboard, wireless LAN, wireless ethernet. but it is limited in range to only a few hundred meters. Depending on frequency radio offers different bandwidths.
- Terrestrial microwave: In terrestrial microwave two antennas are used for communication. A focused beam emerges from an antenna and is recieved by the other antenna, provided that antennas should be facing each other with no obstacle in between. For this reason antennas are situated on high towers. Due to curvature of earth terristial microwave can be used for long distance communication with high bandwidth. Telecom department is also using this for long distance communication. An advantage of wireless communication is that it is not required to lay down wires in the city hence no permissions are required.
- Satellite communication: Satellite acts as a switch in
sky. On earth VSAT(Very Small Aperture Terminal) are used to transmit
and recieve data from satellite. Generally one station on earth
transmitts signal to satellite and it is recieved by many stations on
earth. Satellite communication is generally used in those places where
it is very difficult to obtain line of sight i.e. in highly irregular
terristial regions. In terms of noise wireless media is not as good as
the wired media. There are frequency band in wireless communication and
two stations should not be allowed to transmit simultaneously in a
frequency band. The most promising advantage of satellite is
broadcasting. If satellites are used for point to point communication
then they are expensive as compared to wired media.

Data Encoding
Digital data to analog signals
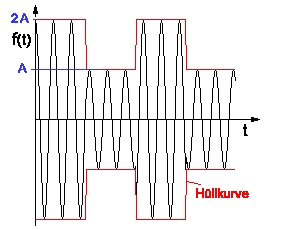
A modem (modulator-demodulator) converts digital data to analog signal. There are 3 ways to modulate a digital signal on an analog carrier signal.- Amplitude shift keying (ASK): is a form of modulation which represents digital data as variations in
the amplitude of a carrier wave. Two different amplitudes of carrier frequency represent '0' , '1'.
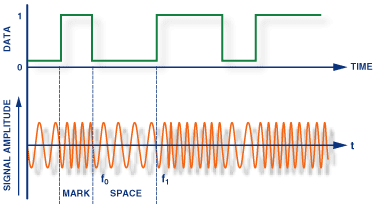
- Frequency shift keying (FSK): In Frequency Shift Keying, the change in frequency define different digits.
Two different frequencies near carrier frequency represent '0' ,''1'.
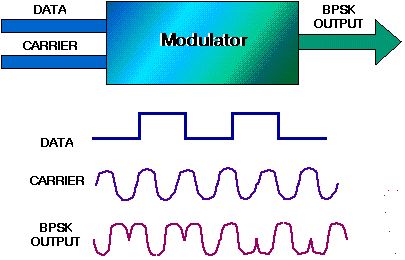
- Phase shift keying (PSK): The phase of the carrier is discretely varied in relation either to a reference
phase or to the phase of the immediately preceding signal element, in accordance with data being transmitted. Phase
of carrier signal is shifted to represent '0' , '1'.
Digital data to digital signals
A digital signal is sequence of discrete , discontinuous voltage pulses. Each pulses a signal element. Encoding scheme is an important factor in how successfully the receiver interprets the incoming signal.Encoding Techniques
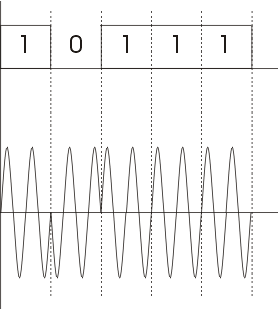
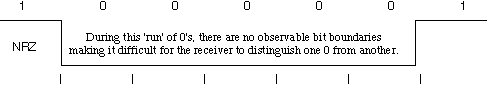
Following are several ways to map data bits to signal elements.- Non return to zero(NRZ) NRZ codes share the property that voltage level is constant during a bit interval.
High level voltage = bit 1 and Low level voltage = bit 0. A problem arises when there is a long
sequence of 0s or 1s and the volatage level is maintained at the same value for a long time. This creates a problem on
the recieving end because now, the clock synchronization is lost due to lack of any transitions and hence, it is difficult
to determine the exact number of 0s or 1s in this sequence.
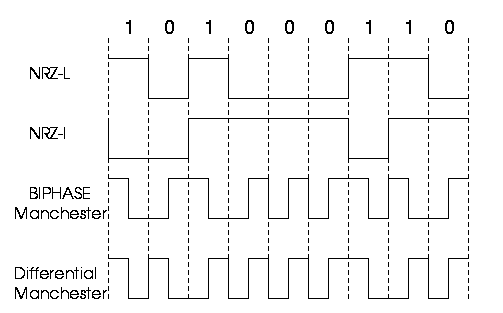
The two variations are as follows:- NRZ-Level: In NRZ-L encoding, the polarity of the signal changes only when the incoming signal changes from a 1 to a 0 or from a 0 to a 1. NRZ-L method looks just like the NRZ method, except for the first input one data bit. This is because NRZ does not consider the first data bit to be a polarity change, where NRZ-L does.
- NRZ-Inverted: Transition at the beginning of bit interval = bit 1 and No Transition at beginning of bit interval = bit 0 or vicecersa. This technique is known as differential encoding.
- Biphase encoding: It has following characteristics:
- Modulation rate twice that of NRZ and bandwidth correspondingly greater. (Modulation is the rate at which signal level is changed).
- Because there is predictable transition during each bit time,the receiver can synchronize on that transition i.e. clock is extracted from the signal itself.
- Since there can be transition at the beginning as well as in the middle of the bit interval the clock operates at twice the data transfer rate.
- Biphase-manchester: Transition from high to low in middle of interval = 1 and Transition from low to high in middle of interval = 0
- Differential-manchester: Always a transition in middle of interval. No transition at beginning of interval=1 and Transition at beginning of interval = 0
- 4B/5B Encoding: In Manchester encoding scheme , there is
a transition after every bit. It means that we must have clocks with
double the speed
to send same amount of data as in NRZ encodings. In other words, we may
say that only 50% of the data is sent. This performance
factor can be significantly improved if we use a better encoding
scheme. This scheme may have a transition after fixed number
of bits instead of every other bit. Like if we have a transition after
every four bits, then we will be sending 80% data of actual capacity.
This is a significant improvement in the performance.
This scheme is known as 4B/5B. So here we convert 4-bits to 5-bits, ensuring at least one transition in them.
The basic idea here is that 5-bit code selected must have :
- one leading 0
- no more than two trailing 0s
4-bit Data 5-bit code 4-bit Data 5-bit code 0000 11110 1000 10010 0001 01001 1001 10011 0010 10100 1010 10110 0011 10101 1011 10111 0100 01010 1100 11010 0101 01011 1101 11011 0110 01110 1110 11100 0111 01111 1111 11101
Of the remaining 16 codes, 7 are invalid and others are used to send some control information like line idle(11111), line dead(00000), Halt(00100) etc.
There are other variants for this scheme viz. 5B/6B, 8B/10B etc. These have self suggesting names.
- 8B/6T Encoding: In the above schemes, we have used two/three voltage levels for a signal. But we may altogether use more than three voltage levels so that more than one-bit could be send over a single signal. Like if we use six voltage levels and we use 8-bits then the scheme is called 8B/6T. Clearly here we have 729(3^6) combinations for signal and 256(2^8) combinations for bits.
- Bipolar AIM: Here we have 3 voltage levels: middle,upper,lower
- Representation 1: Middle level =0 Upper,Lower level =1 such that successive 1's will be represented alternately on upper and lower levels.
- Representation 2 (pseudoternary): Middle level =1 Upper,Lower level=0
Analog data to digital signal:
The process is called digitization. Sampling frequency must be at least twice that of highest frequency present in the the signal so that it may be fairly regenerated. Quantization - Max. and Min values of amplitude in the sample are noted. Depending on number of bits (say n) we use we divide the interval (min,max) into 2(^n) number of levels. The amplitude is then approximated to the nearest level by a 'n' bit integer. The digital signal thus consists of blocks of n bits.On reception the process is reversed to produce analog signal. But a lot of data can be lost if fewer bits are used or sampling frequency not so high.- Pulse code modulation(PCM): Here intervals are equally spaced. 8 bit PCB uses 256 different levels of amplitude. In non-linear encoding levels may be unequally spaced.
- Delta Modulation(DM): Since successive samples do not differ very much we send the differences between previous and present sample. It requires fewer bits than in PCM.
Digital Data Communication Techniques:
For two devices linked by a transmission medium to exchange data ,a high degree of co-operation is required. Typically data is transmitted one bit at a time. The timing (rate, duration,spacing) of these bits must be same for transmitter and receiver. There are two options for transmission of bits.- Parallel All bits of a byte are transferred simultaneously on separate parallel wires. Synchronization between multiple bits is required which becomes difficult over large distance. Gives large band width but expensive. Practical only for devices close to each other.
- Serial Bits transferred serially one after other.Gives less bandwidth but cheaper. Suitable for transmission over long distances.
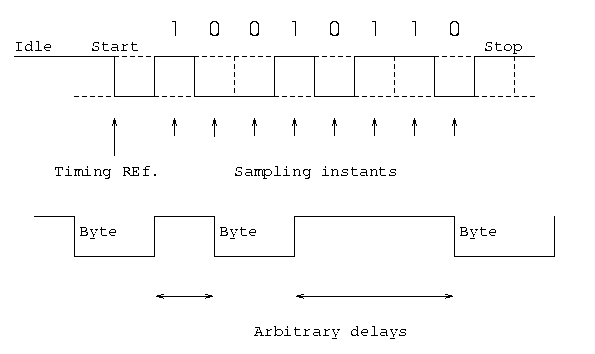
- Asynchronous: Small blocks of bits(generally bytes) are sent
at a time without any time relation between consecutive bytes
.when no transmission occurs a default state is maintained
corresponding to bit 1. Due to arbitrary delay between consecutive
bytes,the time occurrences of the clock pulses at the receiving
end need to be synchronized for each byte. This is achieved by
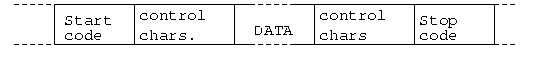
providing 2 extra bits start and stop.
Start bit: It is prefixed to each byte and equals 0. Thus it
ensures a transition from 1 to 0 at onset of transmission of
byte.The leading edge of start bit is used as a reference for
generating clock pulses at required sampling instants. Thus each
onset of a byte results in resynchronization of receiver clock.
Stop bit: To ensure that transition from 1 to 0 is always present at beginning of a byte it is necessary that default state be 1. But there may be two bytes one immediately following the other and if last bit of first byte is 0, transition from 1 to 0 will not occur . Therefore a stop bit is suffixed to each byte equaling 1. It's duration is usually 1,1.5,2 bits.
Asynchronous transmission is simple and cheap but requires an overhead of 3 bits i.e. for 7 bit code 2 (start ,stop bits)+1 parity bit implying 30% overhead.However % can be reduced by sending larger blocks of data but then timing errors between receiver and sender can not be tolerated beyond [50/no. of bits in block] % (assuming sampling is done at middle of bit interval). It will not only result in incorrect sampling but also misaligned bit count i.e. a data bit can be mistaken for stop bit if receiver's clock is faster.
- Synchronous -
Larger blocks of bits are successfully transmitted.Blocks of data are either treated as sequence of
bits or bytes. To prevent timing drift clocks at two ends need to be synchronized.This
can done in two ways:
- Provide a separate clock line between receiver and transmitter. OR
- Clocking information is embedded in data signal i.e. biphase coding for digital signals.
No comments:
Post a Comment
its cool